8 AWS Security Best Practices for 2024 [Cloud Security Checklist Included]
Safeguarding AWS resources and ensuring cloud security requires following essential practices. These include creating an incident response plan, implementing access controls, keeping AWS updated, and ensuring compliance with regulations. Embracing these practices enhances security and protects against cyber threats.

You are on the cloud, but are you leveraging the cloud?
Nowadays, securing cloud resources can be a tough nut to crack, especially when it's about AWS security.
Though being a market pioneer, AWS continuously spearheads the development of more robust and comprehensive ways to assemble your cloud architecture.
Infrastructure as a Service (IaaS), Software as a Service (SaaS), and Platform as a Service (PaaS) computing options mean organizations running AWS have numerous applications and cloud services that need expert configuration and security.
But, as we know, innovation nurtures value; it must also carefully adhere to the right policies, standards, and best practices to manage security in AWS. This is why it's important to enact a better cloud security strategy that helps you make sure your data, code, and workload stay secure.
To make the most of AWS's built-in security features, experts recommend following the time-tested practices in our AWS security checklist.
💡 Bonus: AWS is the only commercial cloud that has its service offerings and supply chain vetted and accepted as safe enough for top-secret workloads.
The Best Practices to Uphold Your AWS Cloud Security Strategy
If your organization’s architecture is completely built on AWS, your AWS security strategy will be inclusive of all AWS nuances. However, if your organization migrated to AWS in recent times, you need to keep up with the new AWS security practices in your daily routine.
Clearly said, AWS security is a one-of-a-kind challenge.
Cloud’s benefit of being flexible and scalable, leads to the ability to spin resources as per the requirements. Whereas, this simultaneously complicates security, making it more difficult to manage than that developed for static on-premises systems.
Therefore, take time and manifold your efforts to craft a strategy that addresses all the ways an AWS cloud can be put in jeopardy.
So, your AWS strategy should envelope elements like:
- Visibility across cloud environments
- A layered approach to cyber security
- Cloud security platforms and tools
- DevSecOps strategies that integrate with software development lifecycle and more.
Once you have defined a strategy, it’s high time to put it into effect with AWS security practices.
Let’s see tried and true methods valuable to organizations hosting data in the cloud.
- Threat and Incident Response Planning
- Cloud Security Control
- Scaling Security in Workflow
- Detection, monitoring, and alerting
- Encryption
- Data backups
- Up-to-date AWS
- Compliance planning
AWS Security Best Practices
Though this list doesn’t seem comprehensive, the pocketed eight AWS practices are the ones we have found time-tested for organizations operating in the cloud.
Outlining an AWS Incident Response Planning
Simply put, “An incident response plan is an array of instructions for addressing a security incident”.
Over a decade, "Assume Breach" has been the war hoop (a pretty literal one) for cybersecurity professionals. However, in a recent blog from Forbes, it can be easily explained that any system, person, or account at any time can be a potential attack vector.
With such numerous attack vectors, it's essential to brace oneself for at least one vector.
Once you "assume breach," imagine where an attacker would probably go to maximize their profit. Like, towards your biggest critical data store.
This mirrors the imperativeness of crafting a thorough incident and response plan. A robust plan will minimize the collateral damage of a cyber attack. Though the ideal situation would be to avoid a breach, a comprehensive incident response will circumscribe when and where a breach will occur, how to identify it as soon as possible, the steps needed to mitigate it, and how your company will recover. We also recommend the following:
- Launch forensic workstations
- Share Amazon Cloud Watch logs
Cloud Security Control
“Thrive safely in the Cloud.”
Cloud security is a broad term, relatively encompassing all the best practices, processes, and strategies that must be followed to secure cloud environments and mitigate the impact of a malicious attack. Learning what is cloud security can provide a foundational understanding to implement these strategies effectively.
The most crucial and basic security control you must have in place in your AWS environments is access controls. Giving the least privileged cloud access to your organization's people who need it and limiting or removing the ones who don’t need it – especially those outside your organization - is a good practice for identifying access management (IAM).
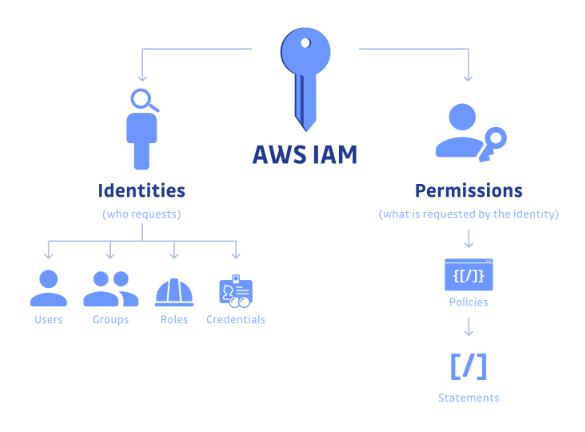
You can easily achieve this by practicing the following:
- Allowing single sign-on (SSO)
- Securely store passwords in an encrypted vault
- Rotating access keys frequently
- Requiring multi-factor authentication (MFA)
- Keeping strong passwords of at least 14 characters with a blend of uppercase and lowercase letters, symbols, and numbers.
- Creating IAM users instead of sharing AWS account root user credentials
Besides, review access privileges to substantiate that nobody has more or less access than they require.
Scale Security in Development Workflow
An AWS security strategy is undoubtedly fragmentary if it only addresses your cloud infrastructure. Creating a strategy that embodies every aspect of development is equally important, from coding the infrastructure to application coding to its runtime.
Adopting a Secure SDLC approach ensures that security is woven into each phase of the development lifecycle, helping to identify and address vulnerabilities before applications reach production.
Infrastructure as code and code scanning solutions are proven approaches that integrate effective security within your AWS development workflows. Moreover, you can quickly identify security gaps and mistakes while your coders are coding, eventually helping you resolve issues before your applications reach production.
Detection, monitoring, and alerting
With malicious attacks coming in different shapes and forms, implementing solid detection, monitoring, and watchful processes and solutions is an unskippable element of AWS application security.
Furthermore, AWS has numerous tools that act as a boon in building your strategy, like:
- Amazon Macie - This tool provides AI-driven discovery, categorization, and security for any sensitive data identified in your environments and provides alerts if any unauthorized access is detected.
- Amazon CloudWatch - This tool is an AWS monitoring solution offered by AWS for monitoring services for AWS resources and other applications you run on AWS.
- Amazon GuardDuty - This tool helps in managing threats along with monitoring workloads for any odd activity that might portray potential red flags.
- AWS Security Hub - This tool offers a comprehensive view of high-priority security alerts and compliance statuses across AWS accounts.
- AWS Config Rules - This tool helps in evaluating the configuration of a resource compared to your pre-determined configuration rules so it’s easy to identify any potential compliance concerns.
Encryption
Regulatory bodies are in dire need of encryption in numerous circumstances. Though it’s no longer a nice-to-have feature, it adds an extra layer of security to your data.
If your access controls fail, encryption safeguards your data from anyone who has acquired it, despite their motivation. In addition, leveraging AWS Graviton2 instances can enhance the security of your AWS environment by providing powerful and efficient ARM-based processors specifically designed for cloud workloads. Here, AWS Encryption comes in the big picture. AWS encryption is available across all their services, and it also offers tangible key management so you can choose if AWS will manage your keys or you will have complete access.
Whatever choice you make, you should design or pick an encryption and keys management system to make sure that encrypted data and decryption keys are stored securely and under stringent protocols.
Have Data backups
Shadow characters and natural disasters have the potential to disturb, destroy, or disperse your data, leaving your enterprise with a bumble. So, it’s essential to back up your data to ensure you can easily restore crucial information immediately.
Furthermore, AWS backup is also a considerable choice to keep your data secure. It supports numerous additional services, including S3 buckets, EBS volumes, DynamoDB tables, etc. Furthermore, you can automate your backups from the console, develop backup policies and requirements, and establish guidelines for other AWS resources through tagging systems.
You can easily get your hands on this on Amazon EC2 free tier.
Up-to-date AWS
Often, keeping your AWS up-to-date is a foregone conclusion. But, applying patches and updates is important to the security of your cloud environment.
Some IT giants avoid this practice or deprioritize it in favor of more prioritized matters. Just don’t let that root in your organization.
Instead, you must keep your AWS servers patched, even if they are not public. After all, outdated infrastructure offers an escape to hackers, and you don’t want to look up to something as a missed security patch to mark the difference between another monotonous day in cybersecurity and a breach.
Compliance planning
In regulatory industries like finance and health, it’s crucial to comply with privacy and security laws encompassing personally identifiable information, data privacy, and financial data.
AWS supports cyber-security compliance standards, like FedRAMP, GDPR, HIPAA/HITECH, and FIPS 140-2. Indeed, with the shared responsibility model, you can ensure your data, cloud workloads, and infrastructure configurations adhere to the guidelines of regulatory bodies to maintain cloud compliance.
Finally
To truly resolve today’s cloud security challenges, it’s imperative to pick cloud-native security practices. Besides, these practices ensure that security is built-in from the beginning of the development process through production, providing different layers of security and constant monitoring for malicious attacks and vulnerabilities.
But today’s organizations have greater cybersecurity threats than ever before. So, by outlining a dynamic AWS security strategy, establishing a cloud-native security solution, and employing these eight time-tested practices, you are inching towards keeping your application and organization away from any threats.


%201-1.webp?width=148&height=74&name=our%20work%20(2)%201-1.webp)


.png?width=344&height=101&name=Mask%20group%20(5).png)








.png?width=352&name=Semantic%20Search%20and%20RAG%20(2).png)