iOS based Biometric Local Authentication
The article discusses iOS-based biometric local authentication, focusing on Face ID and Touch ID technologies. It highlights their integration into apps for secure, user-friendly authentication. Key benefits include enhanced security, convenience, and speed. The article also covers implementation guidelines, best practices, and the importance of safeguarding user data within iOS ecosystems.

From the last couple of years, Security is playing a very crucial role in the mobile domain. The mobility service provider is providing a feature to verify the user identity by scanning a unique body part like a finger, palm, face or iris or by speaking.
With each major version release of iOS, Apple ships on an excellent range of recent technologies and frameworks. So in iOS 7 and iPhone 5S Apple introduced a biometric Local authentication technology. Using that users can unlock the device and make different purchases from the AppStore. In iOS 8, the mobilty service providers can use the fingerprint sensor authentication mechanism for login or authenticate their applications.
Why are we discussing this?
On 12th Sep 2017, Apple introduced a brand new flagship phone the “iPhone X” with a robust new login system. Apple is ditching Touch ID in favor of an automatic face recognition system battery-powered by a brand new camera array and a specially changed A11 chip. Many applications are currently using TouchID only, and after the release of iPhone X, all those mobile application development are not supported. So let’s get a quick introduction of TouchID authentication and FaceID authentication.
Quick Introduction
TouchID:
For unlocking the Apple devices Apple Inc. released a unique feature of fingerprint recognition, using this user can make purchases within the Apple digital media stores (the iTunes Store, the App Store, and also the iBooks Store), and authorize Apple Pay online or in apps. Apple says fingerprint scanned information is for storage locally in an exceedingly secure enclave on the Apple A7, A8, A8X, A9, A9X, A10, A10X or A11 processors chips, not within the cloud, a design choice supposed to form it tough for users to access the fingerprint data externally.
Touch ID is available there into the home button, of laser-cut sapphire crystal, and doesn't scratch (scratching would block Touch ID from working). The stainless-steel detection ring detects the user's finger while not pressing it. The feature doesn't work while not contact with this ring. The user's finger may be moving in any direction, and it'll still be read. Apple says it will read sub-epidermal skin layers, and it'll be simple to line up and can improve with each use. The sensing element passes a little current through one's finger to make a "fingerprint map" of the user's corium. Up to five fingerprint maps will be essential within the Secure territory.
FaceID:
As the next step in Local Authentication Apple Inc. Introduce and release FaceID a Facial recognition system for the iPhone X. It's a kind of identity verification technology in AI services which is supposed to succeed Touch ID, a fingerprint-based system. FaceID includes two modules, first one projects a grid with 30,000 and more infrared dots onto a user's face, and the second one reads the pattern to substantiate or deny access. This generates a 3D facial map stored in an exceedingly natural, secured space of the device's processor, inaccessible by Apple itself. Over the time the system can learn the changes in a user's face, and can successfully acknowledge the user while carrying makeup, glasses, spectacles, scarves, hats or with changes in the beard. The system doesn't work with eyes closed.
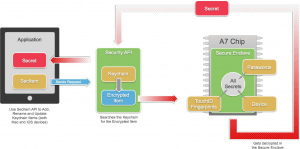
Requirements:
Touch ID and Face ID are a part of the Local Authentication framework, So following are the things we need to check before implementation :
- Check device capability for supporting biometric authentication.
- If device support biometric then system start a check now with the access request and prompt the alert with a reason why we’re asking. For Touch ID, we have to write the string in code, and for Face ID into our Info.plist file(NSFaceIDUsageDescription Key).
- Once the authentication is complete it means this is the device's owner so we can unlock the app, otherwise, we show a failure message.
Let’s Start: The TouchID/FaceID is a feature on a new framework called Local Authentication, that provides facilities for authentication from users with fixed security policies.
Local Authentication Framework
The Local Authentication framework has only one class that is LAContext.
LAContext :
An LAContext object represents an authentication context and supplies a programmatic interface for evaluating authentication policies and access controls, managing credentials, and invalidating authentication contexts.
First, create an authentication context, and Check the biometric sensor availability and setup the biometric authentication. Then we need to provide the policy to evaluate.
LAPolicy :
- OwnerAuthenticationWithBiometrics: It puts restriction to use only biometric authentication to authenticate the device owner.
- deviceOwnerAuthentication: It will allow the application to verify the device owner using biometric or the device password.
LABiometryType :
- FaceID: It puts restriction to use only FaceID to authenticate the device owner.
- TouchID: It puts restriction to use only TouchID to authenticate the device owner.
Checking Biometric availability:
LAContext provides a method for monitoring the biometric availability. So the canEvaluatePolicy(_:error:) method return false if it fails because, if biometric authentication is not available, policy evaluation fails.
- LAError.biometryNotAvailable: Authentication could not start because the device does not support biometric authentication.
- LAError.biometryNotEnrolled: Authentication could not start because the user has not enrolled in biometric authentication.
- LAError.biometryLockout: Authentication could not continue because the user is now under lock out of biometric authentication, due to failing authentication too many times.
Evaluating Authentication Policies:
LAContext provides method for estimating the specified policy. So the evaluatePolicy(_:localizedReason:reply:) method return true if policy evaluation succeeded, otherwise false.
evaluatedPolicyDomainState: Returns the current state of the evaluated policy domain.
Evaluating Access Controls:
LAContext provides a method for evaluating the access control for a given operation. So the evaluateAccessControl(_:operation:localizedReason:reply:) method return true if policy evaluation succeeded, otherwise false.
Managing Credentials:
LAContext provides a method to set an application credential for use when evaluating authentication. So the setCredential(_:type:) method return true if the credential was set, otherwise false. Setting the parameter to nil removes any existing credential of the specified type. isCredentialSet(_:) method return a Boolean value indicating whether the specified credential type is set.
Invalidating the Authentication Context:
LAContext provides a method invalidate() to Invalidates the authentication context. Calling this method stops any pending policy evaluations, causing them to fail with the LAError.Code.systemCancel error code.
LAError:
Errors issued by the LocalAuthentication framework.
Hire the best Mobile Application Development Company!
We at Signity Solutions have years of experience working on mobile application development. So, if you are also looking for the mobile app development agency, we have the best mobile app developers in India at your service. Feel free to outsourcing to India and reach us here, and we will revert at the earliest.


%201-1.webp?width=148&height=74&name=our%20work%20(2)%201-1.webp)


.png?width=344&height=101&name=Mask%20group%20(5).png)